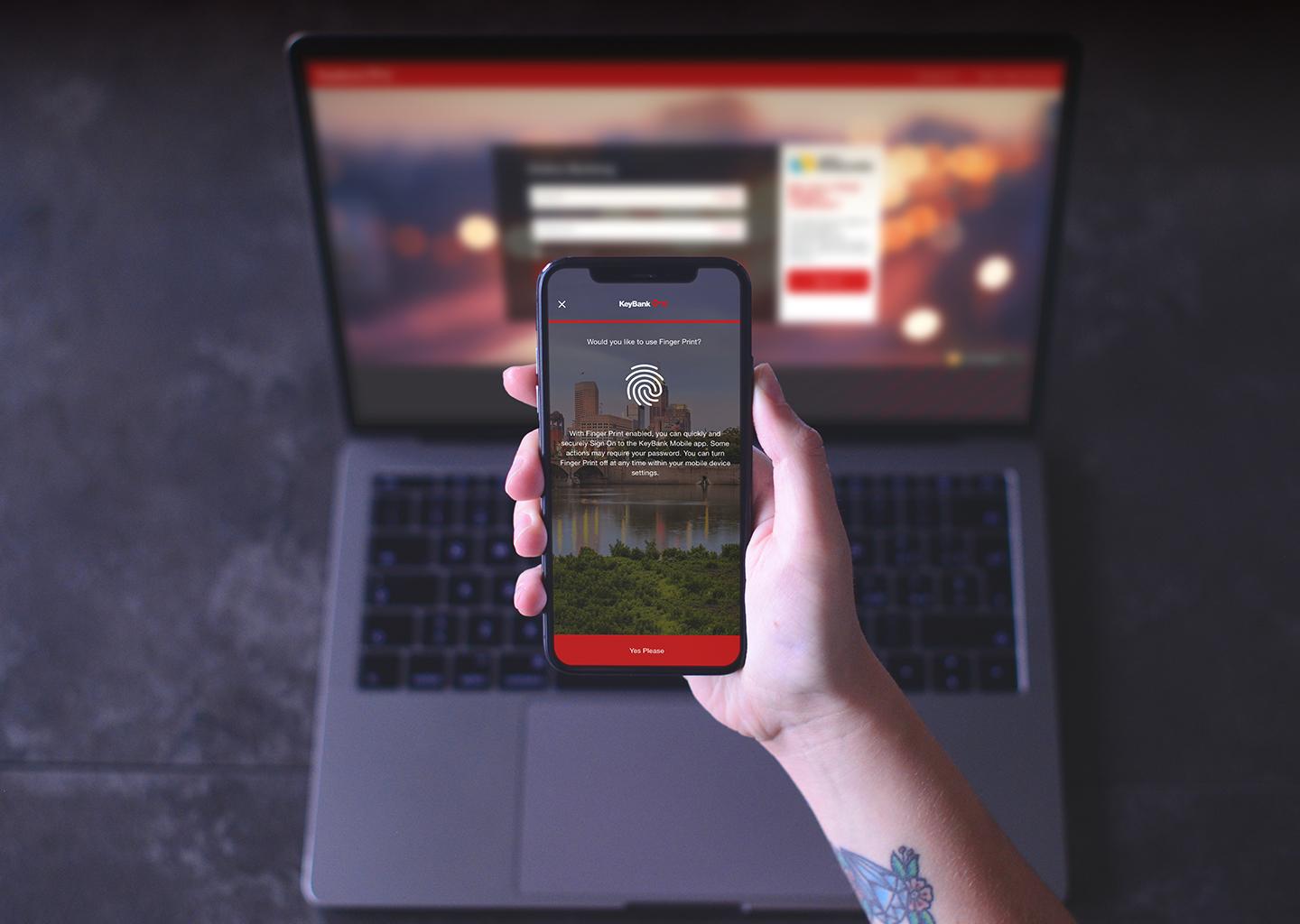
About Photon’s Guide to Security Transformation
Securing digital with Photon’s cybersecurity experiences
By 2020, cybercrime will cost the global economy over $1 trillion2 and 60% of digital businesses will suffer major service failures because of IT security teams’ inability to manage digital risk.
If an organization suffers a security breach, customers may hesitate to provide personal
information online, resulting in disruption of the analytics-driven, real-time, personalized digital
experiences that consumers expect at every interaction. Those customers will switch to another
organization’s online or mobile banking to get better customer experiences and data security. In this guide, we reveal the significance of cybersecurity
Download this cybersecurity guide to quickly learn about
-
Why security transformation is critical for financial organizations
-
Top 10 vulnerabilities in web applications and mobile applications
-
Top 10 vulnerabilities in iOS and Android payment technology
-
Top 10 web app and mobile app vulnerabilities in insurance
-
2 ways you can level up your security
-
3 case studies

Connect with Photon to learn more about Security-as-a-Service (SECaaS).
Photon’s end-to-end security transformation services
- Application security, framework evaluation, and threat management
- Federated identity and relationship management over cloud
- Governance, risk and compliance management
- SMAC security, malware protection, and proactive threat management
- Endpoint cybersecurity, SIEM, log monitoring, and mitigation
- Security consulting, vulnerability prediction and data analytics
Photon’s cybersecurity expertise
- Half of a million vulnerabilities classified in our Security Assurance Portal across 6,500+ test cases and 20 domains (e.g. Banking; Healthcare; Retail)
- Transactional Security and Compliance for Payment Gateways
- MITM (Man-in-the-Middle) attack protection
- Associate-facing, customer-facing and web application security
- EMM (Enterprise Mobility Management) solutions
- Access controllers; REST and WS security infrastructure
- Cloud security, Federated Identity Management, and SSO
Photon’s key security differentiators
- Collaboration portal for assessment; suggestions for remediation
- Mentor development teams continuously advising business teams
- Vulnerability dashboards and notifications; Prediction modeling
- Assessment of 3rd party frameworks; On-demand reporting
"IT security is a keystone of digital transformation—one that can make or break a business’s competitiveness, customer trust, and digital resilience.”
Mukund Balasubramanian
CTO at PHOTON

A deeper look into digital

Delivering secure & seamless CX with Photon CIAM experiences
Create a unified customer identity

5 essential steps to improve omnichannel security
Turn IT security into a competitive differentiator

The digital transformation framework
Download now to adapt digital at the core of your business


Download our whitepaper to adopt CIAM approach to create value-added customer experiences